|

|
|
 |
| ¡¡ |
 |
Content Sharing based on Personal Information in Virtually secured Space |
| |
 |
2008
. 08 ~ current |
|
|
 |
| ¡¡ |
|
1. Introduction
User generated contents (UGC) are shared in an open space like social media where users can upload and consume contents freely. Since the access of contents is not restricted, the contents could be delivered to unwanted users or misused sometimes. In this research, we propose a method for sharing UGCs securely based on the personal information of users. With the proposed method, virtual secure space is created for contents delivery. The virtual secure space allows UGC creator to deliver contents to users who have similar personal information and they can consume the contents without any leakage of personal information.
2. Virtual Secure Content System based on User Information
There are two choices user can make. One is to upload contents without encryption for unlimited consumption to any users. The other is our proposed method which encrypts data with secret key. In this case, content creators allow users to decrypt and consume the contents only if they have similar personal information including contents preference and profile. |
|
|
|
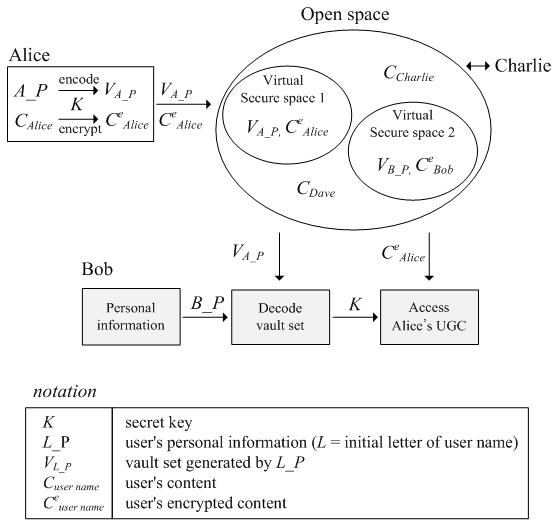
Fig. 1. The consumption process of UGC in the open space
|
|
In Fig. 1, the
open space refers to the web space such as Youtube. Since the access of the
contents in the open space is not restricted, users can consume contents
anytime anywhere. In this space, encrypted contents (CeAlice and CeBob) and
unencrypted contents (CCharlie and CDave) can be
uploaded according to the choices content creators made. For the encrypted content, corresponding
vault set (VA_P and VB_P) is
uploaded together. In real applications, instead
of encryption, content can be visibly watermarked or restricted by providing
preview only. The access to the encrypted contents are given to
users according to their personal information (user profile and contents
preference), and users with similar personal information can be defined as a
virtual group, i.e. virtual space. This space, generated by the vault set, is
only opened to users with similar personal information. Thus, the virtual space
can be secured by grouping the contents according to personal information. In the view of content categorization, each
virtual secure space is a category generated by the combination of personal
information. Therefore, we can generate more various and flexible categories
than using the current categorization method. The following will show possible scenarios that could occur.
Alice is a user (or UGC creator) who
wants to provide her content to the group of people who have similar personal
information. To do so, she uploads UGC (CeAlice) that is
encrypted by her secret key (K) and the vault
set (VA_P)
generated by her personal information. Her profile and content preference are the
features of her personal information. Uploaded Alice¡¯s vault set creates a
virtual secure space and allows accessibility to only users who have similar
personal information.
Bob is a user who wants to consume Alice¡¯s content. In order to consume the
content, Bob downloads Alice¡¯s vault set (VA_P) and
decrypts it with his personal information. If his
personal information is mostly overlapped with Alice¡¯s, he can decode the vault set and acquire the secret key which allows the
decryption of the content. Hence, Bob can freely consume the contents inside
the virtual secure space generated by Alice where this space is opened to only
users who have similar personal information with Alice, like Bob. From the
perspective of Alice, this can be seen as a method for limiting the accessibility
to the contents consumers by creating the virtual space.
Lastly, Charlie and Dave are users who want to provide their contents to the
public. The contents of Charlie and Dave (CCharlie and CDave) are
uploaded without any encryption. This method is currently well used in most of
UGC sites, where consumption of the contents is unlimited but cannot protect the contents being delivered to unwanted
users.
|
|
2. Virtual Secure Content System based on User Information
To use the mentioned personal information items as an input of fuzzy vault scheme, we defined personal information items (PII) and assigned 16 bit-value to each item. N number of PII values corresponding to his personal information at the encoder and decoder side is used as an input. Let the set of PII values at the encoder side be the T={t1, t2, ¡¦,tN}, and at the decoder side be the Q={q1, q2,¡¦,qN}.
Fig. 2 represents the fuzzy vault encoder using PII value. As seen in the figure, fuzzy vault encoder generates a vault set with the list of PII value and secret key as an input. The set of user¡¯s PII value is T={t1, t2, ¡¦,tN} which is identical to user¡¯s personal information item list, T in Fig.2. 128-bit Advanced Encryption Standard (AES) key is utilized as a secret key to protect the contents.
|
|

|
|
Fig.
2. Vault set generation |
|
The fuzzy vault decoder uses PII values an input and if more than D+1 number of PII values is the same as that of encoding side, the original secret key can be acquired which guarantees the successful decryption of the content. Here, D denotes the degree of polynomial that is constructed in polynomial construction module in Fig. 2. The set of queryt user¡¯s PII value is Q={q1, q2,¡¦,qN}, which is identical with Query user information item list Q in Fig 3.
|
|

|
|
Fig.
3. Secret key generation |
|
3. Experiments |
|
To simplify the experiment, we assume that each user has 12 PII values. If nine PII values are identical with each other, i.e. PII values used to encode a vault set and query user¡¯s PII values are identical, the encrypted content can be consumed. To realize this, the number of PII value is 12 in the fuzzy vault encoder. The degree of encoder polynomial is eight and the number of chaff point is 298. We assumed that six users, including the content creator, are accessing the encrypted content. Detailed personal information of the six users used in the experiment is presented in Table 1.
|
|
Sub-category
|
User A
|
User B
|
User C
|
User D
|
User E
|
User F
|
|
S1
|
P4
|
P5
|
P5
|
P4
|
P5
|
P4
|
|
S2
|
P7
|
P7
|
P7
|
P8
|
P8
|
P8
|
|
S3
|
P11
|
P11
|
P11
|
P11
|
P11
|
P11
|
|
S4
|
P32
|
P16
|
P16
|
P32
|
P32
|
P32
|
|
S5
|
P39
|
P39
|
P39
|
P43
|
P39
|
P39
|
|
S6
|
P90
|
P90
|
P90
|
P90
|
P90
|
P90
|
|
S7
|
P211
|
P209
|
P209
|
P211
|
P211
|
P211
|
|
S8
|
P214
|
P214
|
P214
|
P214
|
P214
|
P214
|
|
S9
|
P245
|
P231
|
P231
|
P245
|
P245
|
P245
|
|
S10
|
P276
|
P261
|
P276
|
P276
|
P276
|
P276
|
|
S11
|
P289
|
P289
|
P289
|
P289
|
P289
|
P289
|
|
S12
|
P299
|
P299
|
P299
|
P310
|
P299
|
P299
|
|
|
Table 1. Private information of user A, B, C, D, E and F |
|
Table 2 show the decoding result according to the degree of polynomial used in vault set generation. In Table 2, the positive represents the number of sets when
the redundancy is zero after CRC decoding at the decoder side in Fig 3. Likewise, the negative represents the
number of sets when the redundancy is not zero. If the CRC decoding result is positive, the probability of a set containing
the proper secret key is very high.
The experiment proves that the virtual secure space generated by personal
information of user A is opened to user D, E and F, but not to user B and C. Since user A, D, E and F have more than eight identical personal
information items, the encrypted content and the vault set generated by their
own personal information create a secure space where user B and C have no accessibility. In this space, user A, D, E and F can upload their contents freely and share
them securely. If we apply this
concept to every user in the open space, we can form various flexible groups.
|
|
D
|
Consumer
|
Identical PII to
user A
|
Candidate set
|
Positive set
|
Negative set
|
Authentication
|
|
6
|
user B
|
7
|
792
|
1
|
791
|
Yes
|
|
user C
|
8
|
792
|
8
|
784
|
Yes
|
|
user D
|
9
|
792
|
36
|
756
|
Yes
|
|
user E
|
10
|
792
|
120
|
672
|
Yes
|
|
user F
|
11
|
792
|
330
|
462
|
Yes
|
|
7
|
user B
|
7
|
495
|
0
|
495
|
No
|
|
user C
|
8
|
495
|
1
|
494
|
Yes
|
|
user D
|
9
|
495
|
9
|
486
|
Yes
|
|
user E
|
10
|
495
|
45
|
450
|
Yes
|
|
user F
|
11
|
495
|
165
|
330
|
Yes
|
|
8
|
user B
|
7
|
220
|
0
|
220
|
No
|
|
user C
|
8
|
220
|
0
|
220
|
No
|
|
user D
|
9
|
220
|
1
|
219
|
Yes
|
|
user E
|
10
|
220
|
10
|
210
|
Yes
|
|
user F
|
11
|
220
|
55
|
165
|
Yes
|
|
9
|
user B
|
7
|
66
|
0
|
66
|
No
|
|
user C
|
8
|
66
|
0
|
66
|
No
|
|
user D
|
9
|
66
|
0
|
66
|
No
|
|
user E
|
10
|
66
|
1
|
65
|
Yes
|
|
user F
|
11
|
66
|
11
|
55
|
Yes
|
|
10
|
user B
|
7
|
12
|
0
|
12
|
No
|
|
user C
|
8
|
12
|
0
|
12
|
No
|
|
user D
|
9
|
12
|
0
|
12
|
No
|
|
user E
|
10
|
12
|
0
|
12
|
No
|
|
user F
|
11
|
12
|
1
|
11
|
Yes
|
|
|
Table 2. Decoding result according to the degree of polynomial |
|
|
|
3. Security Issue |
|
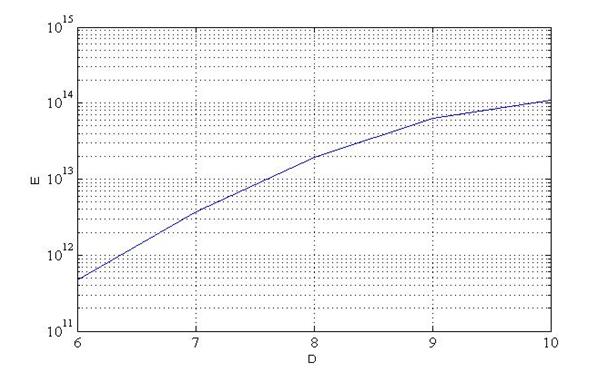
We consider the possibility of personal information leakage. For the security considerations, let us assume that the adversary wants to break the virtual secure space using brute force attack simulated by our experimental environment. For a given personal information table, the adversary can break the virtual secure space by evaluating all combination sets (1.94x1013 sets) at maximum which takes about 1.60x105 years when the degree of polynomial is 8 (Note one set evaluation time is about 0.26 sec at 3.4GHz CPU). The required number of evaluations to break the virtual secure space according to degree of the polynomial is presented in Fig. 3. In this figure, D denotes the degree of the polynomial and E denotes the number of evaluation to break virtual secure space.
|
|
|
|
Fig. 3. Evalutation for brute force attack |
|
|
|
 |
|
|
 |
 Hosik Sohn Hosik Sohn |
 sohnhosik@kaist.ac.kr sohnhosik@kaist.ac.kr |
|
Ph.D. Candidate in Dept. of EE in KAIST
Senior Researcher in IVY Lab in KAIST
|
| |
| |
 Experience of Research projects Experience of Research projects |
|
Virtual secure space using Fuzzy vault with user preference
|
|
Privacy preservation of biometric template
|
|
Privacy protection Surveillance camera system
|
| 
|
Measurement of Visual quality metrics in Scalable video
|
| 
|
Video Adaptation using quality metrics
|
|
 Research Interest Research Interest |
|
Biometric security, Scalable Video Coding, Video Quality, Multimedia adaptation,
Video surveillance
|
| |
|
|
|
| ¡¡ |
| |
 |
| ¡¡ |
|
Hosik Sohn, Yong Man Ro, and Konstantinos N. Plataniotis, ¡°Content Sharing based on Personal Information in Virtually Secured Space,¡± IWDW 2008, pp.401-413, Nov.10~12, 2008, Busan, Korea
|
|
Hosik Sohn, Yong Man Ro, and Konstantinos N. Plataniotis, "Content Sharing between Home Networks by using Personal Information and Associated Fuzzy Vault Scheme," IEEE Transaction on Consumer Electronics (submitted)
|
|
|
| | |